In a recent announcement at the Enterprise Mobility Blog, https://blogs.technet.microsoft.com/enterprisemobility/2017/08/31/changes-to-the-token-lifetime-defaults-in-azure-ad/, there will be a change for default settings to the Token Lifetime Defaults in Azure Active Directory for New Tenants only. This change will not affect existing old Tenants.
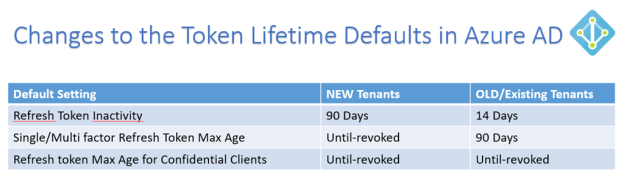
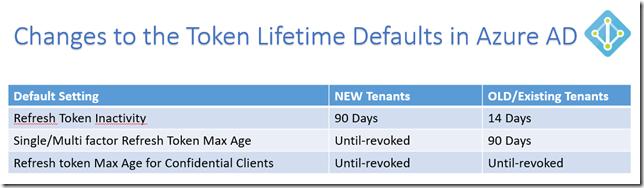
I have summarized the changes in this table:
This is great news for many customers to remove user frustration over authentication prompts when refresh tokens expired after a period of inactivity. For example, if I havent used an App on my mobile phone for 14 days, I have to reauthenticate with my work/school account again to get a new Access Token and Refresh Token. Some Apps I use quite often, like Outlook and OneDrive, and by keeping active the Refresh Token will be continously renewed as well together with the Access Token (which by default is valid for 1 hour). For my existing tenant this would mean that keeping active, and at least using the Refresh Token inside the 14 Days, I will get new Access and Refresh Tokens, but after 90 Days the Single and/or Multi factor Refresh Token Max Age will be reached, and I have to reauthenticate again in my Apps.
Some Apps I will naturally use more rarely, for example Power BI, Flow, PowerApps etc. (this will be different for each user type), but I risk having to reauthenticate every time if I only access these Apps every other week.
So for New Tenants this has now changed, as Refresh Tokens will be valid for 90 Days, and if you use the Refresh Token inside that period, you will get 90 more days. And furthermore, the Max Age for Single/Multi factor Refresh Token will have a new default of Until-revoked, so basically it will never expire.
Keep in mind though, that Azure AD Administrators can revoke any Refresh Token at any time. Refresh Tokens will also be invalid if the authenticated users password changes or expire. It is also nice to be aware of that every time a Refresh Token is used to get a new Access Token, Conditional Access and Identity Protection from Azure AD will be used to check if the User or Device is in a Compliant State with any policies defined.
A few words on the Confidential Clients also. Confidential Clients are typically Web Apps that are able to securely store Tokens and identity itself to Azure AD, so after the User has Authenticated and actively Consented to access specific Resources, the resulting Access and Refresh Tokens can be used until revoked, as long as the Refresh Token are used at least once inside 90 Days (New Tenants) or 14 Days (Old Tenants).
If you want to read more deep dive on configurable Token Lifetimes, you can follow this link: https://docs.microsoft.com/en-us/azure/active-directory/active-directory-configurable-token-lifetimes.
Azure AD PowerShell examples for changing Token Lifetime Defaults
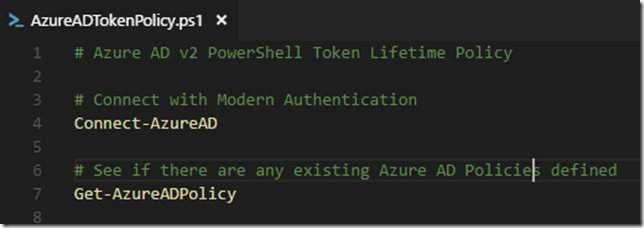
I have created some Azure AD PowerShell V2 examples for how you can change the Token Lifetime Policy defaults in your organization.
First connect to your Tenant and see if there already are defined any policies (normally there would be nothing):
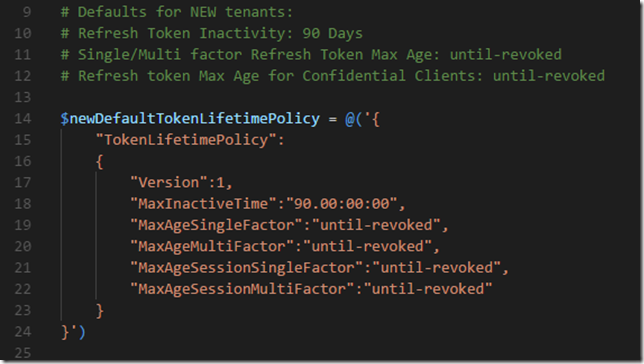
Then lets make a definition that reflects the new defaults for New Tenants:
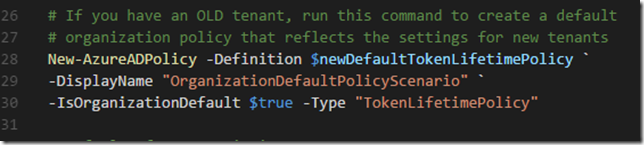
So if you already have an existing old tenant, and you want to change the default policy so that it reflects the new Token Lifetime settings, you can run this command:
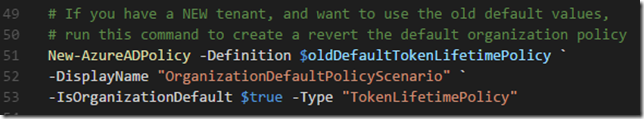
A different scenario, lets say I have a New Tenant, and want to use the old default values instead. I will make a definition that reflects that:
And create a policy using these definitions:
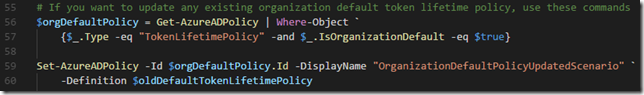
Last, I will leave you with commands for changing any existing Azure AD policies:
The complete list of Azure AD PowerShell CmdLets used and examples can be found here at my Gist repository.
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| # Azure AD v2 PowerShell Token Lifetime Policy | |
| # Connect with Modern Authentication | |
| Connect-AzureAD | |
| # See if there are any existing Azure AD Policies defined | |
| Get-AzureADPolicy | |
| # Defaults for NEW tenants: | |
| # Refresh Token Inactivity: 90 Days | |
| # Single/Multi factor Refresh Token Max Age: until-revoked | |
| # Refresh token Max Age for Confidential Clients: until-revoked | |
| $newDefaultTokenLifetimePolicy = @('{ | |
| "TokenLifetimePolicy": | |
| { | |
| "Version":1, | |
| "MaxInactiveTime":"90.00:00:00", | |
| "MaxAgeSingleFactor":"until-revoked", | |
| "MaxAgeMultiFactor":"until-revoked", | |
| "MaxAgeSessionSingleFactor":"until-revoked", | |
| "MaxAgeSessionMultiFactor":"until-revoked" | |
| } | |
| }') | |
| # If you have an OLD tenant, run this command to create a default | |
| # organization policy that reflects the settings for new tenants | |
| New-AzureADPolicy -Definition $newDefaultTokenLifetimePolicy ` | |
| -DisplayName "OrganizationDefaultPolicyScenario" ` | |
| -IsOrganizationDefault $true -Type "TokenLifetimePolicy" | |
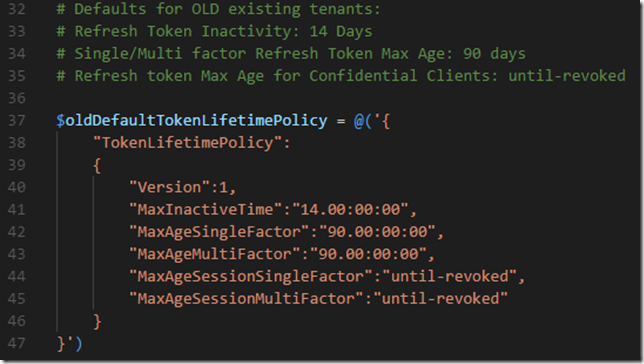
| # Defaults for OLD existing tenants: | |
| # Refresh Token Inactivity: 14 Days | |
| # Single/Multi factor Refresh Token Max Age: 90 days | |
| # Refresh token Max Age for Confidential Clients: until-revoked | |
| $oldDefaultTokenLifetimePolicy = @('{ | |
| "TokenLifetimePolicy": | |
| { | |
| "Version":1, | |
| "MaxInactiveTime":"14.00:00:00", | |
| "MaxAgeSingleFactor":"90.00:00:00", | |
| "MaxAgeMultiFactor":"90.00:00:00", | |
| "MaxAgeSessionSingleFactor":"until-revoked", | |
| "MaxAgeSessionMultiFactor":"until-revoked" | |
| } | |
| }') | |
| # If you have a NEW tenant, and want to use the old default values, | |
| # run this command to create a revert the default organization policy | |
| New-AzureADPolicy -Definition $oldDefaultTokenLifetimePolicy ` | |
| -DisplayName "OrganizationDefaultPolicyScenario" ` | |
| -IsOrganizationDefault $true -Type "TokenLifetimePolicy" | |
| # If you want to update any existing organization default token lifetime policy, use these commands | |
| $orgDefaultPolicy = Get-AzureADPolicy | Where-Object ` | |
| {$_.Type -eq "TokenLifetimePolicy" -and $_.IsOrganizationDefault -eq $true} | |
| Set-AzureADPolicy -Id $orgDefaultPolicy.Id -DisplayName "OrganizationDefaultPolicyUpdatedScenario" ` | |
| -Definition $newDefaultTokenLifetimePolicy | |
| # Look at existing token lifetime polices and settings | |
| $aadTokenLifetimePolicies = Get-AzureADPolicy | Where-Object {$_.Type -eq "TokenLifetimePolicy"} | ` | |
| Select-Object DisplayName, Type, IsOrganizationDefault, Definition | |
| # List existing settings | |
| $aadTokenLifetimePolicies.Definition | ConvertFrom-Json | Select-Object -ExpandProperty TokenLifetimePolicy | ` | |
| Select-Object $aadTokenLifetimePolicies.DisplayName, ` | |
| MaxInactiveTime, ` | |
| MaxAgeSingleFactor, ` | |
| MaxAgeMultiFactor, ` | |
| MaxAgeSessionSingleFactor, ` | |
| MaxAgeSessionMultiFactor |
Hopefully this has been informative and helpful for Azure AD Administrators and others ![]() !
!
I have small doubt in this life time policy update.
Please find my scenario below:
I have created access token first with default expiration as 1hour.
and after 1 hour its got expired and created refresh token and created new policy as below:
New-AzureADPolicy -Definition @(‘{“TokenLifetimePolicy”:{“Version”:1, “MaxAgeSingleFactor”:”until-revoked”}}’) -DisplayName “OrganizationDefaultPolicyScenario” -IsOrganizationDefault 1 -Type “TokenLifetimePolicy”
New-AzureADPolicy -Definition @(‘{“TokenLifetimePolicy”:{“Version”:1,”AccessTokenLifetime”:”1.00:00:00″}}’) -DisplayName “OrganizationDefaultPolicyScenario” -IsOrganizationDefault 1 -Type “TokenLifetimePolicy”
but i think it doesn’t affect the refresh token life time. Refresh token also getting expired in 1 hour.
Apart from this should i want to do anything further ?
Will it update the life time of token belongs to Active directory which i login ?
How to ensure whether updated life time has been updated for particular token ?
Please provide me step by step process .
Until-revoked also will last only for 365 days ?t3Hq^[5.
Please help me to resolve this.
Thanks in advance.
Priyanka, I responded in the thread here: https://blogs.technet.microsoft.com/enterprisemobility/2017/08/31/changes-to-the-token-lifetime-defaults-in-azure-ad/
This is a great article Jan. Thanks. Do you know if it’s possible to view what the token lifetime policies are within existing policies? The get-AzureADPolicy merely lists the policies but not the values. Is there a way we can do that?
Thanks, Eric. I have added a couple of commands to the above linked gist now, for how to list existing settings.
Thanks Jan, for sharing this article. This is very helpful and great article. The configuration we have done for our web api,
New-AzureADPolicy -Definition @(‘{“TokenLifetimePolicy”:{“Version”:1,
“MaxInactiveTime”:”90.00:00:00″,
“MaxAgeSingleFactor”:”until-revoked”,
“MaxAgeMultiFactor”:”until-revoked”,
“MaxAgeSessionSingleFactor”:”until-revoked”,
“MaxAgeSessionMultiFactor”:”until-revoked”}}’)
-DisplayName “WebApiDefaultPolicyScenario”
-IsOrganizationDefault $false
-Type “TokenLifetimePolicy”
How can we test/ confirm this configuration is working in our application ?
Can you please help me on this?
Thanking you
Best Regards,
Very helpfull article, except this seems to be discontinued and not working anymore.
the only alternative is using conditional access??
Yes, you now need to use the sign-in frequency in Conditional Access, the option to add configurable token lifetimes was removed in May 2020.
Hello, how this conditional access works? can you please explain?