I recently installed the new release of Windows Server, version 1709 on my Intel NUC, you can read about that here.
I have installed Project Honolulu for remote server management on that server, but as this Intel NUC is usually located on my home lab network, I want to be able to publish and access the Honolulu website using Azure AD Application Proxy.
As the Windows Server 1709 is Server Core, I need to install and configure the Azure AD Application Proxy Connector silently, and these are the steps I did to do that.
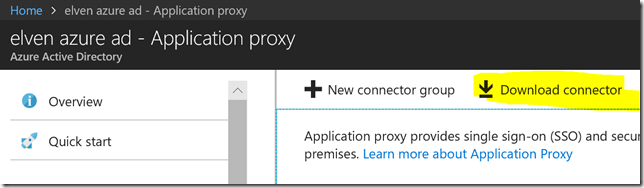
First, you need to download the Application Proxy connector install file, and transfer it to the server. You can access the connector download from Application Proxy section in your Azure AD portal:
After that, run the following command to do a quiet install of the connector, skipping registration interactively:
AADApplicationProxyConnectorInstaller.exe REGISTERCONNECTOR=”false” /q
Next we need to register the Application Proxy connector to Azure AD, and for that we need to run some PowerShell commands. There are two ways this can be done, with a Credential Object, or using an Offline Token. Using Credential is simplest, but has the drawback that you cannot use that method if your Global Administrator account is protected with Azure MFA. Lets look at both methods below.
Using Credential Object:
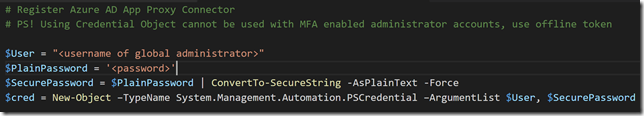
On the Server you want to register the Azure AD App Proxy Connector, start a PowerShell session and run the following commands for setting the Global Administrator user name and password, and then create a Credential Object.
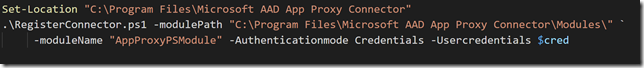
After that, run the following commands to run the RegisterConnector.ps1 script for register the connector using Credential object as authentication:
You can copy the PowerShell commands used above using the Gist linked at the end of this blog post.
Using Offline Token:
If you can’t or don’t want to use a credential object, you have to use a offline token. The following commands will get an access token for the authorization context needed for Application Proxy Connector Registration.
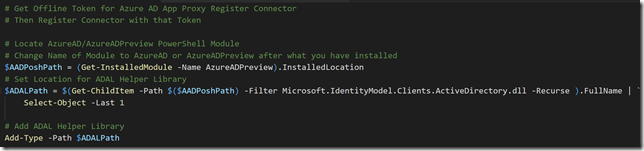
Getting the Token can be run from any client, and then transferred to the server, but you will need to have the Azure Active Directory Authentication Library (ADAL) installed at the machine you are running the PowerShell commands. The easiest way to get the needed libraries installed is to Install the AzureAD PowerShell Module.
The following commands locates the AzureAD (or AzureADPreview) Module, and then finds the ADAL Helper Library: Microsoft.IdentityModel.Clients.ActiveDirectory.dll, and adds that as a Type to the PowerShell session:
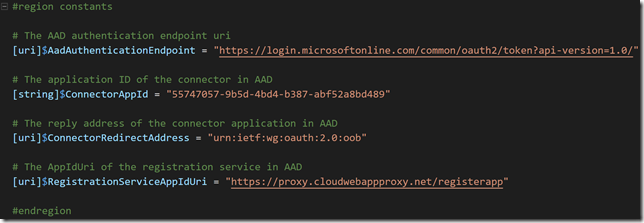
Next, run these commands to define some constants, these values are the same for all tenants:
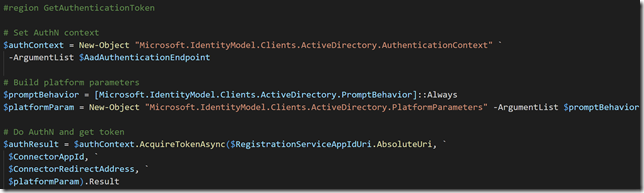
Now we can run these commands for setting the authentication context and then prompt user for AuthN:
Running the above commands will result in an authentication prompt, this is where you would specify your Global Administrator account, and if MFA enabled this will also work:
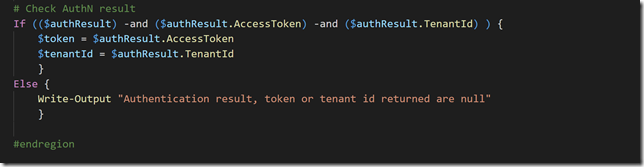
After authenticating we can check the result and save the token and tenantId in variables as shown below:
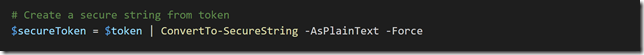
Next, copy the contents of the $token and $tenantId to the Windows Server 1709, and run the following command to create a secure string from the token:
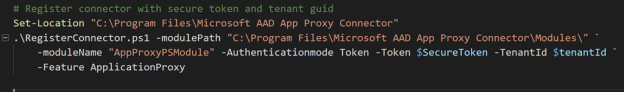
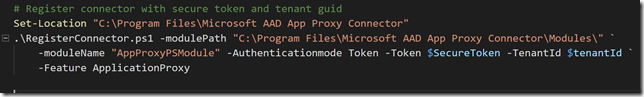
And then run the RegisterConnector.ps1 script with AuthenticationMode as Token and using the secure token and tenant id as parameter values as shown below:
PS! According to the official documentation, there are no description or examples for the mandatory parameter “Feature”, but I found that it accepts the value “ApplicationProxy” as used above.
You can copy the above PowerShell commands from the Gist linked at the end of this blog post.
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| # Register Azure AD App Proxy Connector | |
| # PS! Using Credential Object cannot be used with MFA enabled administrator accounts, use offline token | |
| $User = "<username of global administrator>" | |
| $PlainPassword = '<password>' | |
| $SecurePassword = $PlainPassword | ConvertTo-SecureString –AsPlainText –Force | |
| $cred = New-Object –TypeName System.Management.Automation.PSCredential –ArgumentList $User, $SecurePassword | |
| Set-Location "C:\Program Files\Microsoft AAD App Proxy Connector" | |
| .\RegisterConnector.ps1 –modulePath "C:\Program Files\Microsoft AAD App Proxy Connector\Modules\" ` | |
| –moduleName "AppProxyPSModule" –Authenticationmode Credentials –Usercredentials $cred | |
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| # Get Offline Token for Azure AD App Proxy Register Connector | |
| # Then Register Connector with that Token | |
| # Locate AzureAD/AzureADPreview PowerShell Module | |
| # Change Name of Module to AzureAD or AzureADPreview after what you have installed | |
| $AADPoshPath = (Get-InstalledModule -Name AzureADPreview).InstalledLocation | |
| # Set Location for ADAL Helper Library | |
| $ADALPath = $(Get-ChildItem -Path $($AADPoshPath) -Filter Microsoft.IdentityModel.Clients.ActiveDirectory.dll -Recurse ).FullName | ` | |
| Select-Object -Last 1 | |
| # Add ADAL Helper Library | |
| Add-Type -Path $ADALPath | |
| #region constants | |
| # The AAD authentication endpoint uri | |
| [uri]$AadAuthenticationEndpoint = "https://login.microsoftonline.com/common/oauth2/token?api-version=1.0/" | |
| # The application ID of the connector in AAD | |
| [string]$ConnectorAppId = "55747057-9b5d-4bd4-b387-abf52a8bd489" | |
| # The reply address of the connector application in AAD | |
| [uri]$ConnectorRedirectAddress = "urn:ietf:wg:oauth:2.0:oob" | |
| # The AppIdUri of the registration service in AAD | |
| [uri]$RegistrationServiceAppIdUri = "https://proxy.cloudwebappproxy.net/registerapp" | |
| #endregion | |
| #region GetAuthenticationToken | |
| # Set AuthN context | |
| $authContext = New-Object "Microsoft.IdentityModel.Clients.ActiveDirectory.AuthenticationContext" ` | |
| -ArgumentList $AadAuthenticationEndpoint | |
| # Build platform parameters | |
| $promptBehavior = [Microsoft.IdentityModel.Clients.ActiveDirectory.PromptBehavior]::Always | |
| $platformParam = New-Object "Microsoft.IdentityModel.Clients.ActiveDirectory.PlatformParameters" -ArgumentList $promptBehavior | |
| # Do AuthN and get token | |
| $authResult = $authContext.AcquireTokenAsync($RegistrationServiceAppIdUri.AbsoluteUri, ` | |
| $ConnectorAppId, ` | |
| $ConnectorRedirectAddress, ` | |
| $platformParam).Result | |
| # Check AuthN result | |
| If (($authResult) -and ($authResult.AccessToken) -and ($authResult.TenantId) ) { | |
| $token = $authResult.AccessToken | |
| $tenantId = $authResult.TenantId | |
| } | |
| Else { | |
| Write-Output "Authentication result, token or tenant id returned are null" | |
| } | |
| #endregion | |
| # Create a secure string from token | |
| $secureToken = $token | ConvertTo-SecureString -AsPlainText -Force | |
| # Register connector with secure token and tenant guid | |
| Set-Location "C:\Program Files\Microsoft AAD App Proxy Connector" | |
| .\RegisterConnector.ps1 -modulePath "C:\Program Files\Microsoft AAD App Proxy Connector\Modules\" ` | |
| -moduleName "AppProxyPSModule" -Authenticationmode Token -Token $SecureToken -TenantId $tenantId ` | |
| -Feature ApplicationProxy | |
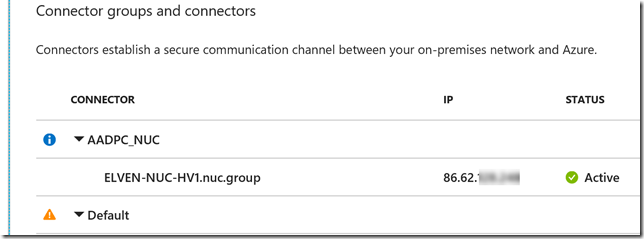
So to recap, after installing the Application Proxy Connector silently on the Windows Server 1709, and then registering the connector, I can now verify in the Azure AD Portal that the connector is available for use. I can see it has a status of Active, from my home IP address, and I have already placed it in a Connector Group.
I’m now ready to publish Azure AD Proxy Apps using this connector, and in my next blogpost I will publish the Project Honolulu management website using this!
Here is the Gist source for the above linked PowerShell commands:
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| # Register Azure AD App Proxy Connector | |
| # PS! Using Credential Object cannot be used with MFA enabled administrator accounts, use offline token | |
| $User = "<username of global administrator>" | |
| $PlainPassword = '<password>' | |
| $SecurePassword = $PlainPassword | ConvertTo-SecureString –AsPlainText –Force | |
| $cred = New-Object –TypeName System.Management.Automation.PSCredential –ArgumentList $User, $SecurePassword | |
| Set-Location "C:\Program Files\Microsoft AAD App Proxy Connector" | |
| .\RegisterConnector.ps1 –modulePath "C:\Program Files\Microsoft AAD App Proxy Connector\Modules\" ` | |
| –moduleName "AppProxyPSModule" –Authenticationmode Credentials –Usercredentials $cred | |
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| # Get Offline Token for Azure AD App Proxy Register Connector | |
| # Then Register Connector with that Token | |
| # Locate AzureAD/AzureADPreview PowerShell Module | |
| # Change Name of Module to AzureAD or AzureADPreview after what you have installed | |
| $AADPoshPath = (Get-InstalledModule -Name AzureADPreview).InstalledLocation | |
| # Set Location for ADAL Helper Library | |
| $ADALPath = $(Get-ChildItem -Path $($AADPoshPath) -Filter Microsoft.IdentityModel.Clients.ActiveDirectory.dll -Recurse ).FullName | ` | |
| Select-Object -Last 1 | |
| # Add ADAL Helper Library | |
| Add-Type -Path $ADALPath | |
| #region constants | |
| # The AAD authentication endpoint uri | |
| [uri]$AadAuthenticationEndpoint = "https://login.microsoftonline.com/common/oauth2/token?api-version=1.0/" | |
| # The application ID of the connector in AAD | |
| [string]$ConnectorAppId = "55747057-9b5d-4bd4-b387-abf52a8bd489" | |
| # The reply address of the connector application in AAD | |
| [uri]$ConnectorRedirectAddress = "urn:ietf:wg:oauth:2.0:oob" | |
| # The AppIdUri of the registration service in AAD | |
| [uri]$RegistrationServiceAppIdUri = "https://proxy.cloudwebappproxy.net/registerapp" | |
| #endregion | |
| #region GetAuthenticationToken | |
| # Set AuthN context | |
| $authContext = New-Object "Microsoft.IdentityModel.Clients.ActiveDirectory.AuthenticationContext" ` | |
| -ArgumentList $AadAuthenticationEndpoint | |
| # Build platform parameters | |
| $promptBehavior = [Microsoft.IdentityModel.Clients.ActiveDirectory.PromptBehavior]::Always | |
| $platformParam = New-Object "Microsoft.IdentityModel.Clients.ActiveDirectory.PlatformParameters" -ArgumentList $promptBehavior | |
| # Do AuthN and get token | |
| $authResult = $authContext.AcquireTokenAsync($RegistrationServiceAppIdUri.AbsoluteUri, ` | |
| $ConnectorAppId, ` | |
| $ConnectorRedirectAddress, ` | |
| $platformParam).Result | |
| # Check AuthN result | |
| If (($authResult) -and ($authResult.AccessToken) -and ($authResult.TenantId) ) { | |
| $token = $authResult.AccessToken | |
| $tenantId = $authResult.TenantId | |
| } | |
| Else { | |
| Write-Output "Authentication result, token or tenant id returned are null" | |
| } | |
| #endregion | |
| # Create a secure string from token | |
| $secureToken = $token | ConvertTo-SecureString -AsPlainText -Force | |
| # Register connector with secure token and tenant guid | |
| Set-Location "C:\Program Files\Microsoft AAD App Proxy Connector" | |
| .\RegisterConnector.ps1 -modulePath "C:\Program Files\Microsoft AAD App Proxy Connector\Modules\" ` | |
| -moduleName "AppProxyPSModule" -Authenticationmode Token -Token $SecureToken -TenantId $tenantId ` | |
| -Feature ApplicationProxy | |

Hey, thank you for that.
Do you know if there is any handy way to monitor availability AAD Proxy? I’m a bit scary to move some apps to AAD proxies, because there is no easy way to monitor functioning of proxy.
Hi Alex. There are no health monitor or alerting for AAD Proxy Connectors as of now, but you can for example monitor the event log for AAD Proxy Connector events with Log Analytics and create your own dashboard/alerts in OMS on that. I have written something in the past on that: https://gotoguy.blog/2015/07/01/how-to-add-azure-ad-application-proxy-connector-log-to-operations-management-suite/
Also, the new Application Proxy cmdlets in the AzureADPreview PowerShell module can get health status on Connectors, so you could script something on that to perform regular checks.