This is a follow up post from an earlier blog post on how to Publish the Cireson Self Service Portal with Azure AD Application Proxy. Is this blog post I will show how to configure a custom domain name for the same published application.
Change External URL
From earlier I already have published this application with the external URL of https://selfservice-skillas.msapproxy.net. I will now change this to our own domain, like this:
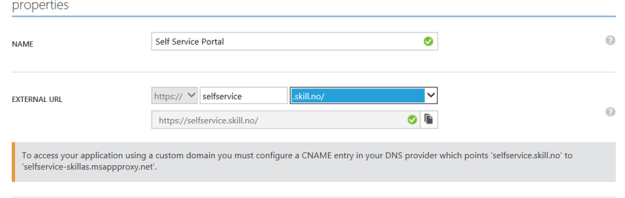
As shown over, I now have to configure the public DNS zone for my domain, with a CNAME record as specified in the screenshot.
Upload SSL Certificate
Following that, I now need to upload a SSL certificate to work with the external URL. Either a Wildcard Cert or a Certificate with common name or subject alternative name containing the external URL can be used.
When uploading the certificate I will need the .pfx file and the password to access the private key:
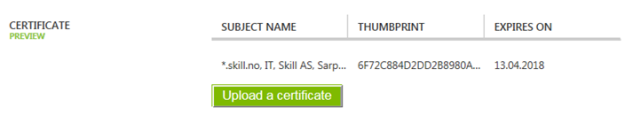
After uploading, I can verify the certificate subject, thumbprint and expiry date:
Testing the External URL
I can now test the external URL, https://selfservice.skill.no.
If I’m already authenticated with Azure AD in this session I will be directed to the external URL, or else I will have to pre-authenticate first as I have configured that.
In the end, everything works as expected with the custom domain name:
Pingback: Publish the Cireson Self Service Portal with Azure AD Application Proxy | SystemCenterPoint
Pingback: Service Manager Self Service Portal – Password Reset with Azure AD Premium | SystemCenterPoint
Pingback: Publish the Service Manager Self Service Portal with Azure AD Application Proxy | SystemCenterPoint
Pingback: Publish the Squared Up SCOM Web Dashboard with Azure AD Application Proxy | SystemCenterPoint
Pingback: Session Recap – Nordic Infrastructure Conference (NIC) 2016 – Publishing Azure AD Applications | SystemCenterPoint
Hello Jan,
Thanks for your post; it helped me get things going.
Do you think it would be possible to provide access to O365 identities in other tenants, based on the B2B functionality, using the Azure Applicaiton proxy to get access to the SCSM portal ‘as a service’?
AzureAD B2B is free and Appliation proxy should be multitenant. MS is saying all the right things here.
I have been trying but get license and other errors.
Thanks for commenting, Jacob. It is a good question, Azure AD App Proxy requires user to have either a Basic or Premium/EMS license assigned. I haven’t really looked into and testing AADAP with B2B scenarios, I might do that later, but for SCSM Portal as a service you would still need directory objects in the hosting AD for each user. These objects could eg. use the mail attribute for WIA and the AADAP application,
whether you those corresponding users are guests or B2B users to the Azure AD that contains the application, I don’t know if it will work for now.
Can this cert be a new certificate from an internal CA with the SAN name included?
Our server admin is worried about uploading the existing cert with Key in PFX form to the cloud and duplicating there as we use it for internal as well.
Yes, it sure can, I’ve tested with that scenario too. Keep in mind though that when using cert from internal CA, your clients that access the App Proxy Url need to trust that Authority
Hi
I am struggling on SSL certificate, How I can create or get a certificate for custom domain name?