This blog post is part of the Blog Series: Power’ing up your Home Office Lights with Power Platform. See introduction post for links to the other articles in the series:
https://gotoguy.blog/2020/12/02/blog-series—powering-up-your-home-office-lights-using-power-platform—introduction/
Now that we have registered the application for Hue Remote API, and stored the client Id and Secret in Azure Key Vault, we can start build the Logic App that will authorize and get access token via Oauth2.
Here is a short video where I introduce the concept:
Create the Logic App and HTTP Trigger
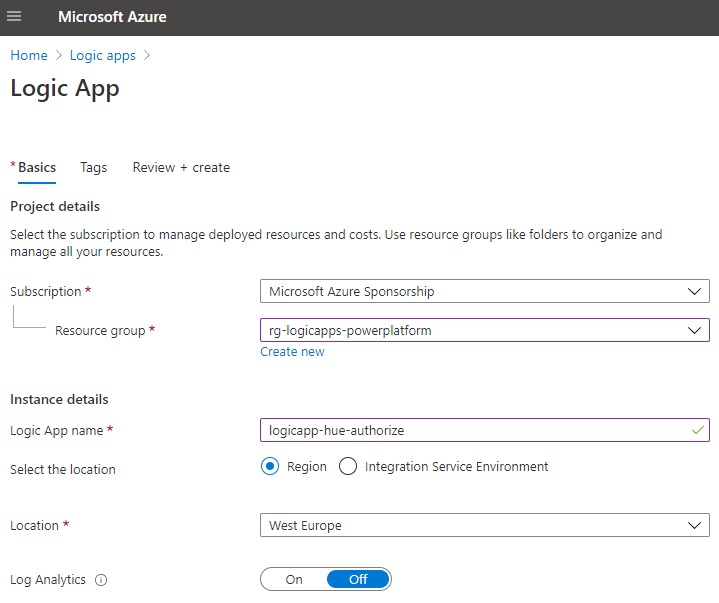
The first thing you need to do, is to create a new Logic App in your Azure subscription. Select the Resource Group you have contributor access to, and give the Logic App a suitable name, as per your naming guidelines:
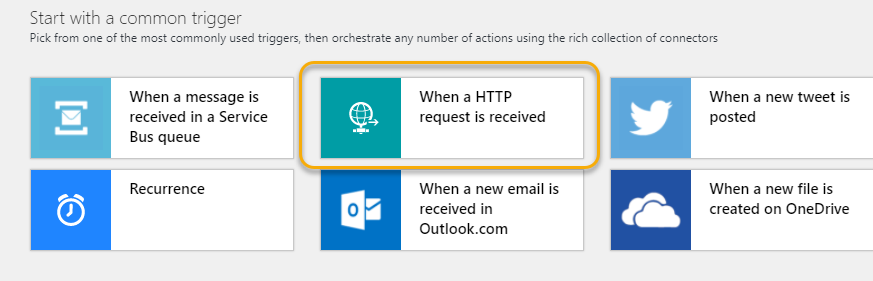
Next, select HTTP request to be the trigger for the Logic App:
After that you will see the following in the Logic App designer:
Make sure you hit Save on the Logic App before the next step. You will now be shown the URL, but first go down to the “Add new parameter” and select Method and GET for method. This way your Logic App will trigger on HTTP GET requests, which is required for the Authorization Code flow with Hue:
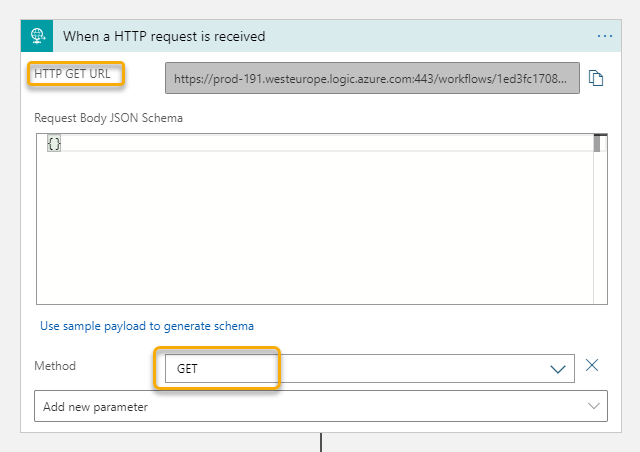
Now copy this URL, and make sure that no one but you can access this URL, as this is a SAS (Shared Access Signature) URL that anyone in the world can send requests to if they know the URL. Save the Logic App.
Go back to your App Registration in the Hue Developers Portal, and change your temporary http://localhost/logicapp Callback URL to your Logic App URL:
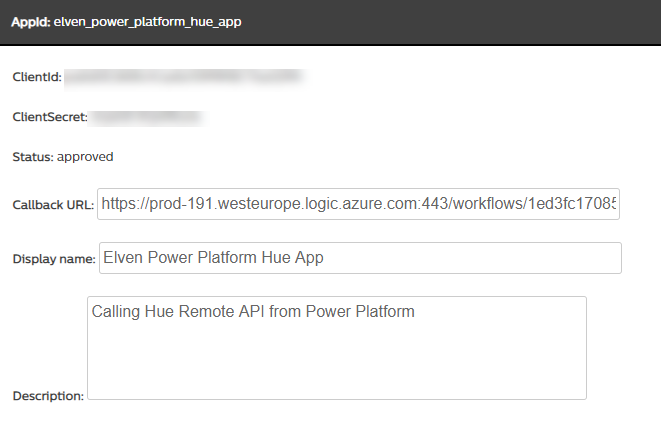
This means that from now on, the Logic App will handle the authorization code for the Hue App. But first we will need to let the Logic App access the Key Vault.
Adding Logic App Identity and Key Vault Access
For the Logic App, under Settings and Identity, set system assigned managed identity to On:
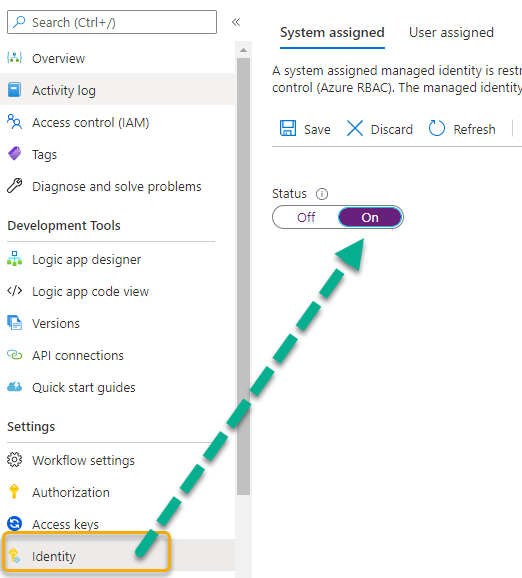
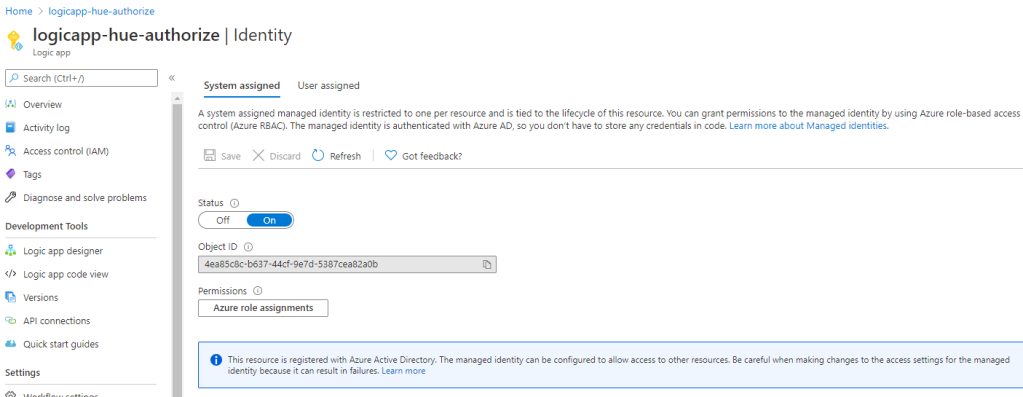
After this setting is saved, you can later see the status and the object id of the service principal.
Next, under your Key Vault, click on Access Policies and Add Access Policy, from there selec the Get, Set and List Secret Management operations, and for principal search for and add the Logic App. This should look like this after adding:
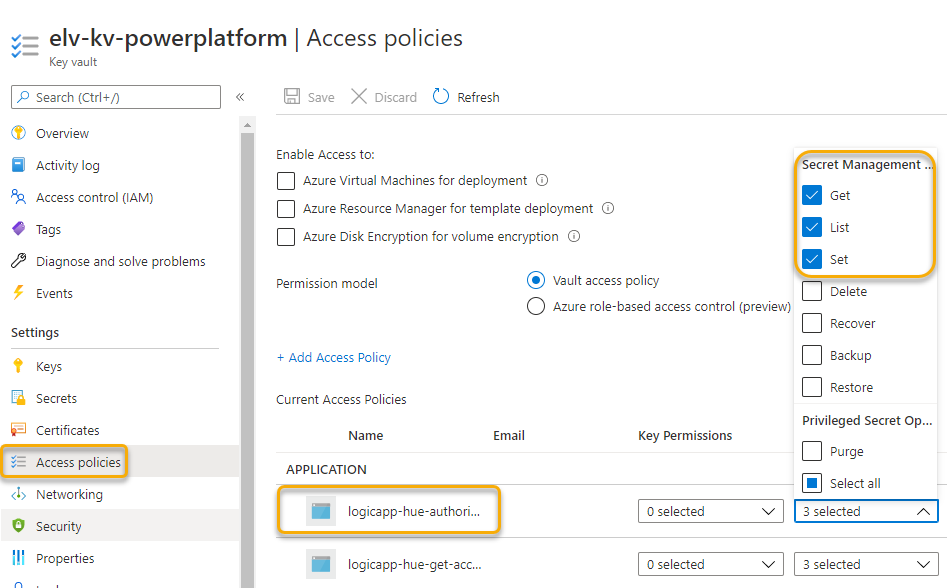
With permissions in place, we are now ready to add actions to the Logic App.
Add Actions for getting Access Token
The first ting we need to do is to get the authorization code after the Hue App registration redirects back to the callback URL. This is returned as a querystring appended to the URL. Add a “Compose” action and use the following expression for getting the request queries:
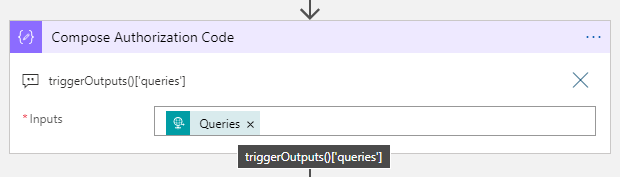
(I’ve added the custom expression to comments for better visibility).
Then we need to get the Client Id and Secret from the Kay Vault. Add a HTTP action next, where we will use the Azure Rest API for getting the secret, and authenticate with the Managed Service Identity:
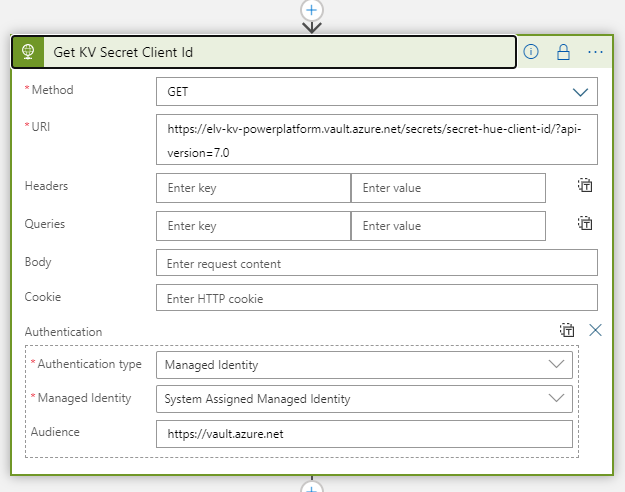
The URI above points to my Azure Key Vault URI, and the specified secret. The documentation for getting secrets can be seen here: Get Secret – Get Secret (Azure Key Vault) | Microsoft Docs.
The same applies to getting the Client Secret, add another HTTP action:
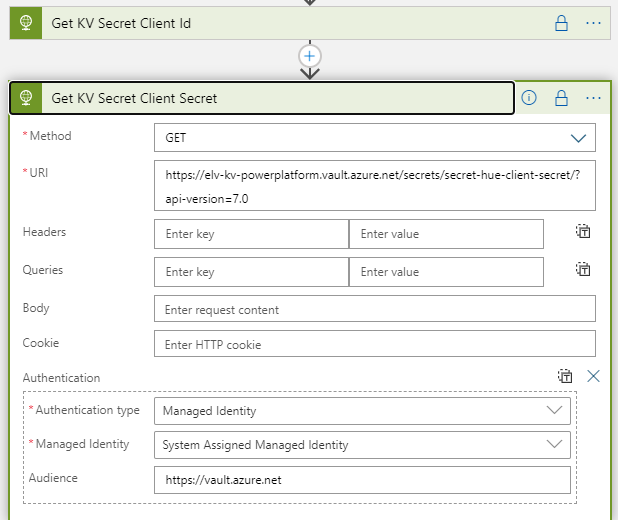
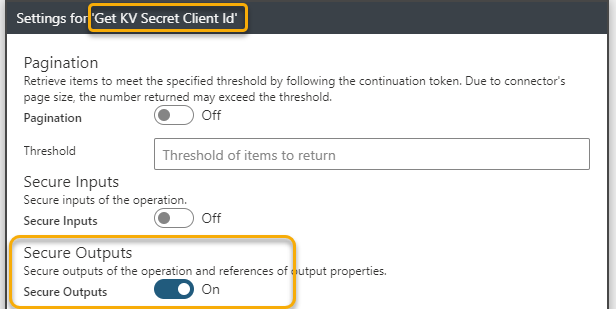
The get an access token from Hue Remote API we must either use Basic Authentication or Digest Authentication. Since I’m running this as a Logic App in a controlled environment and trusting the SSL encryption I will use Basic Authentication. In addition, I will secure the outputs from getting Client Id and Secret from Key Vault, so that other users cannot see those values from the run history:
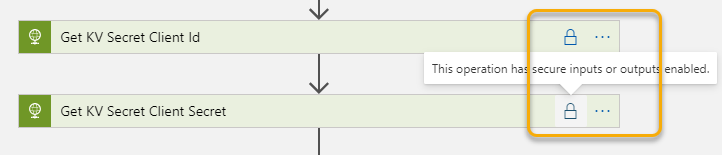
This setting has been enabled for both the actions getting KV Secret Client Id and Client Secret:
For obtaining an Access Token with Basic Authentication the following header is required: Authorization: Basic <base64(clientid:clientsecret)>
This means that we need to base64 encode the clientid + “:” + clientsecret. This can be done using this lengthy expression, here in a “initialize variable” action:
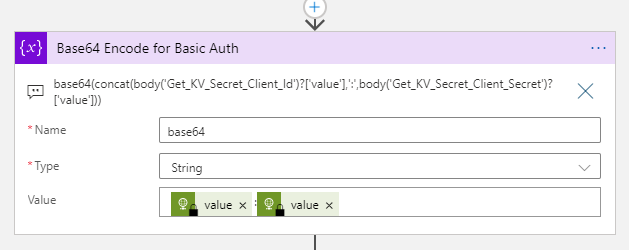
This above action is just for reference though, as the HTTP action supports base64 encoding out of the box. So when posting to the token endpoint, the best way is to use the following:
(PS! Another way to do Basic Authentication in a HTTP action would be to add the Authorization header manually in the Action above with: “Basic <your calculated base64>” as value, and leaving the Authentication type to None.)
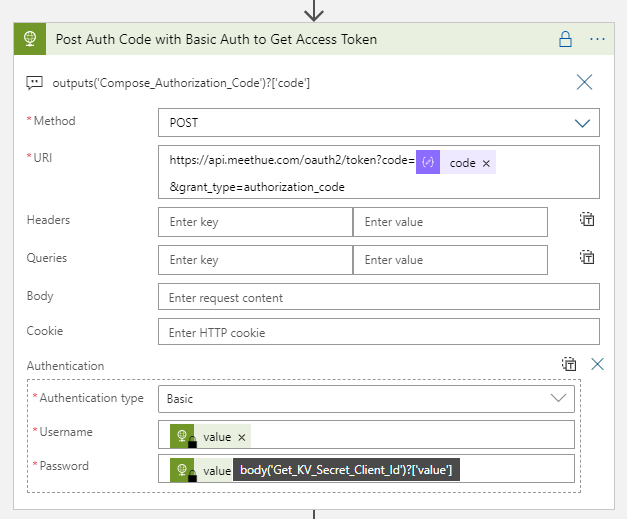
From the above settings, in the URI add the authorization code we got from the request queries earlier, using the expression:
outputs('Compose_Authorization_Code')?['code']
When selecting Authentication type to Basic, the username (client id) and password (secret) will automatically be base64 encoded. The values for username and password are the valies from the Get KV Secret Client actions earlier, in the following format:
body('Get_KV_Secret_Client_Id')?['value']
And this action will return the Bearer Token from Hue Remote API if everything is correctly inputted.
I also make sure that the output of this action is secured from viewing:
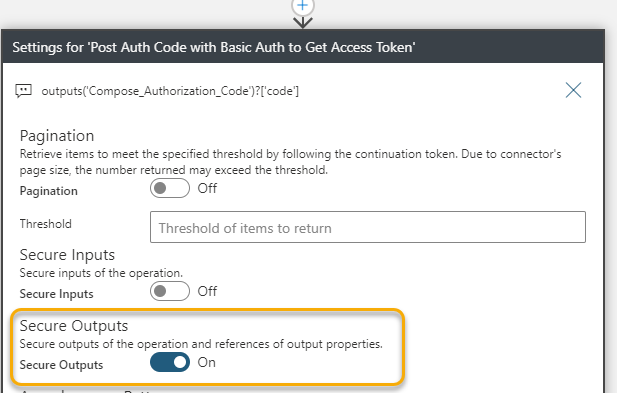
With the Bearer Token now retrieved, the next actions is to calculate the expiry time and write the Token back to the Key Vault secret.
Add Actions for getting expiry time and write Token to Key Vault
The Bearer Token returned by Hue Remote API will be in the format of the following masked response:
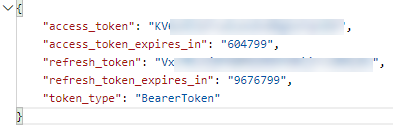
The _expires_in values are in seconds, so that means that the Access Token is valid for 7 days, and the Refresh Token about 112 days. It would then make sense to only refresh the token when needed.
Lets start by calculating when the access_token expires, with the following expression in a Compose action:
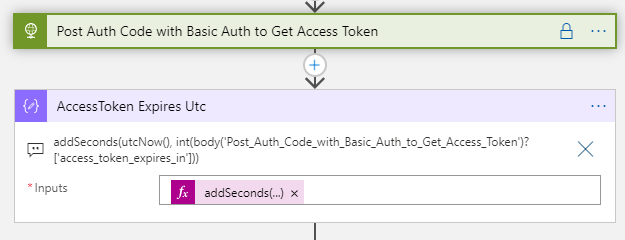
addSeconds(utcNow(), int(body('Post_Auth_Code_with_Basic_Auth_to_Get_Access_Token')?['access_token_expires_in']))
The above expression takes the current time and add the number of seconds for when the access token expires.
This will return a new datetime 7 days ahead. This value will be used to set the expiry time on the Key Vault secret for Bearer Token. By setting an expiry time I can later calculate if I need to refresh the Access Token or not.
But it’s not that easy.. The calculated time above will need to be converted to Epoch (32-bit “Unix”) integer format to be able to set the Key Vault secret “exp” attribute. This isn’t so clear when seeing the API docs, Set Secret – Set Secret (Azure Key Vault) | Microsoft Docs, so took me a little trial and error. And I found great help in this blog article: https://devkimchi.com/2018/11/04/converting-tick-or-epoch-to-timestamp-in-logic-app/.
Based on this I need to convert the timestamp to Ticks (64-bit). Ticks is a built in function in Logic Apps, but to be able to convert to Epoch I will need to calculate the difference in ticks between when the Access Token expire, and the first value of Epoch which is 1970-01-01T00:00:00Z. This is well explained in the above reference blog, but here are my resulting actions.
After calculating the Access Token expiry, I add a compose action which converts this to Ticks:
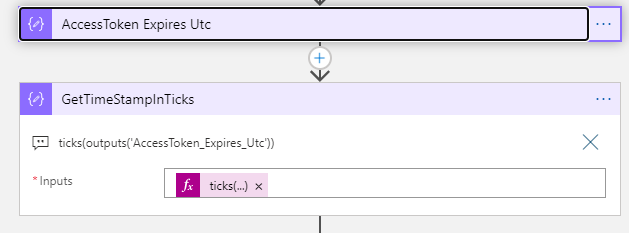
Using the following expression: ticks(outputs('AccessToken_Expires_Utc'))
Then I need to find the 1970-01-01T00:00:00Z value in Ticks:
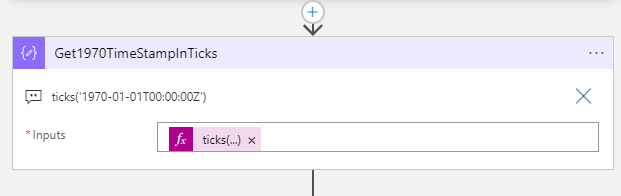

Using this expression: ticks('1970-01-01T00:00:00Z')
Then we can convert this to Epoch by subtracting the two Ticks values calculated above, and divide by 1 million:
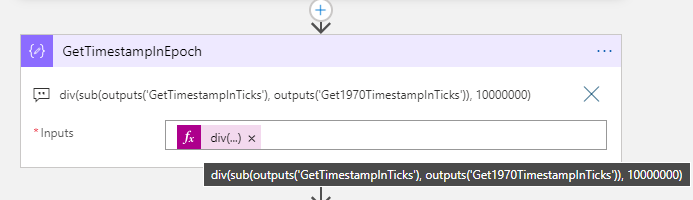
This is the expression used above: div(sub(outputs('GetTimestampInTicks'), outputs('Get1970TimestampInTicks')), 10000000)
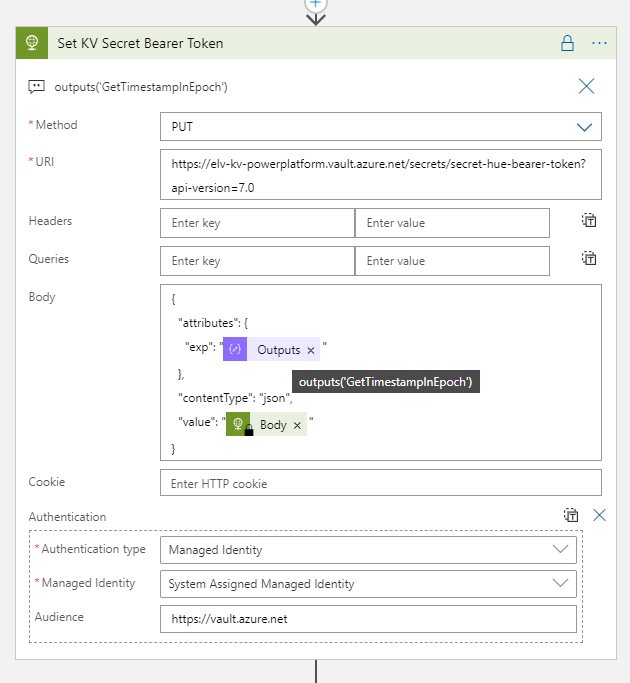
We now have the correct format for the “exp” attribute to update the Key Vault secret. Add a new HTTP action and configure like below:
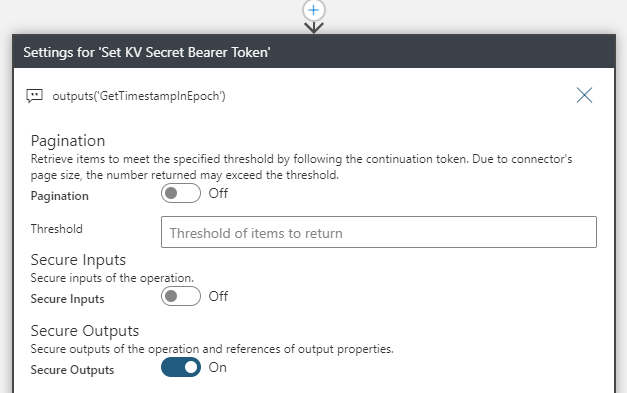
Remember to secure the Output for this action also:
Finally we can finish this Logic App by adding a Response action and do a quick test to verify that everything works as expected.
Adding Response action and verify Logic App
Add a Response action with status code 200 and a body like below:
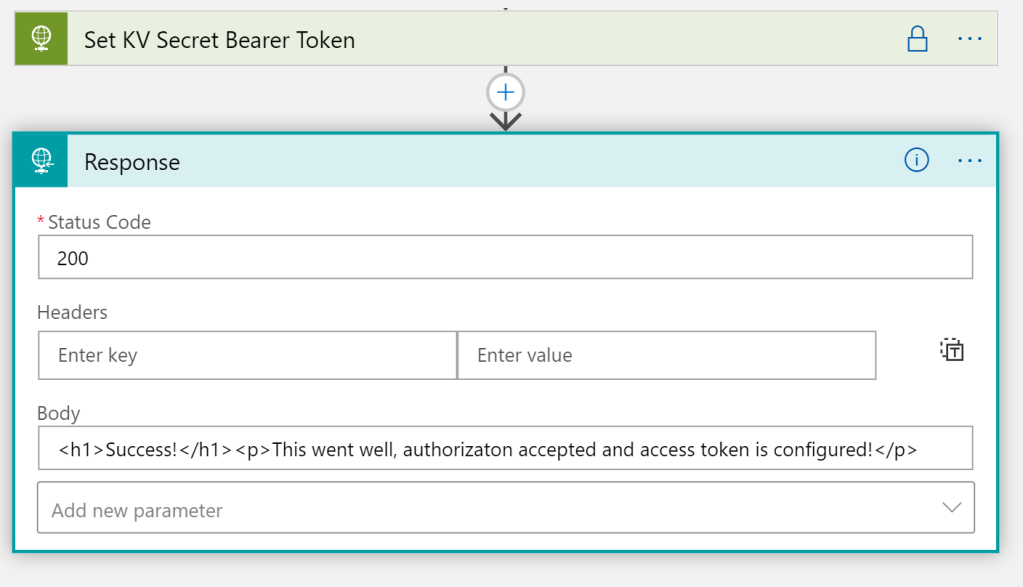
Tips: It can be difficult to troubleshoot the Logic App when securing outputs, so you might hold back in that when testing. It will show your secrets in the run history though, so it might be best to do this in a test enviroment depending on your needs.
Now we can test. Construct the URL for authorizing the App again, like we did in Part 1:
Paste it in the Browser, and after granting access to the App in Hue Developer portal:
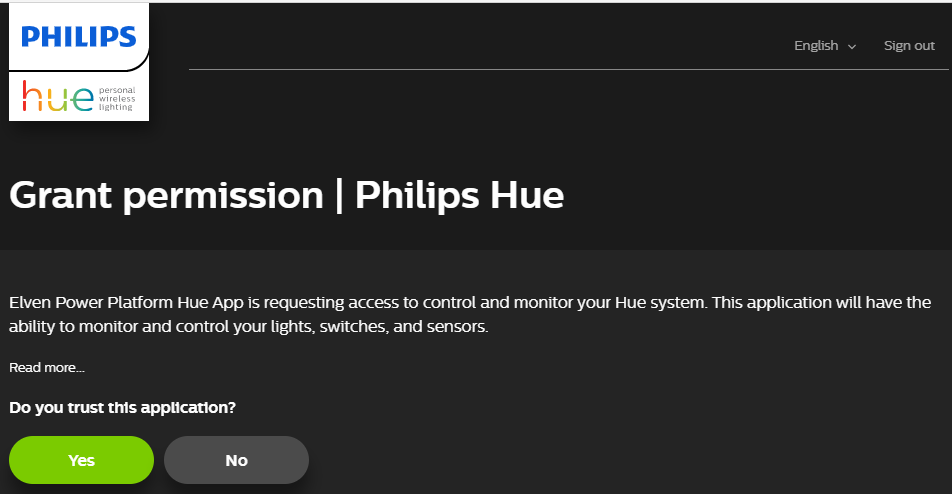
You should be redirected to the Logic App:
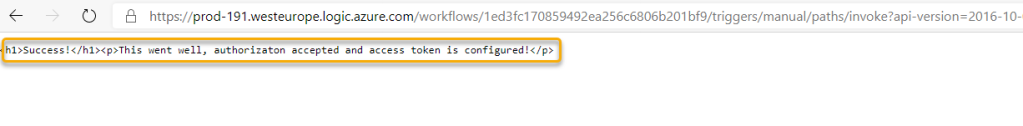
.. and with a respons success!
Looking at the Run history, we can verify the steps were successful:
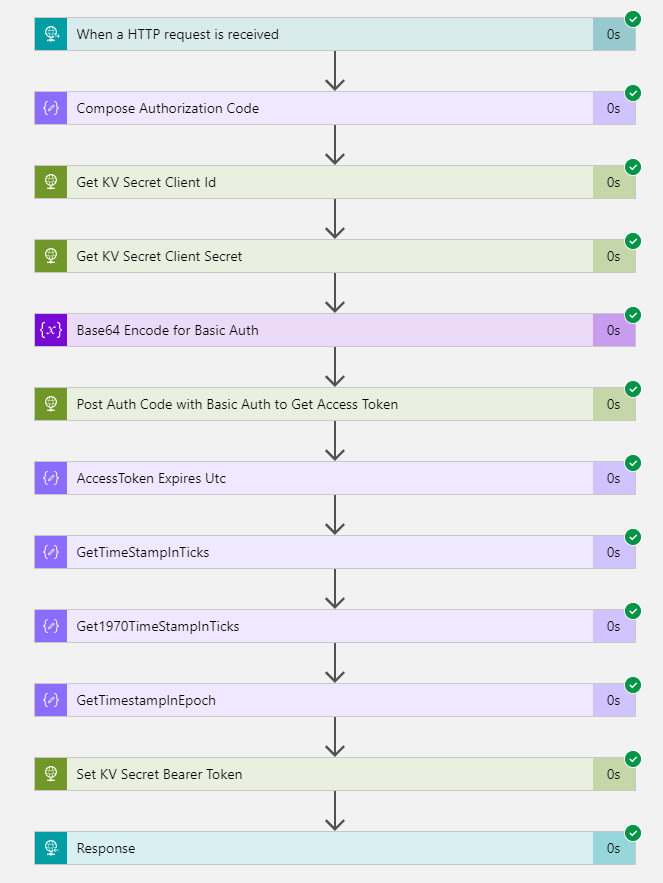
You can also look into the inputs and outputs of the actions, except the actions where we secured the output:
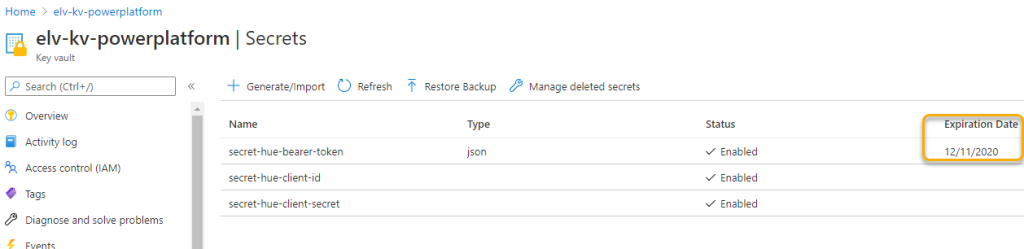
We can also verify that the Key Vault secret storing the Bearer Token has been updated and have an Expiration Date one week forward:
Summary and next steps
That concludes this blog post. Thanks for reading this far, in the next part we will build the Logic App that will respond back the Access Token and renew using Refresh Token if needed.